Tor Browser Download, Installation and Usage
The article will cover basics of torr browser, purpose, how to download, how to install and what steps to take before accessing the dark web. Tor Browser Download
If you wish to learn more about the Dark Web, read the dark web article.
Introduction to Tor Web Browser:
Tor Browser is a browser that allows one to surf the internet anonymously and without censorship. It was developed by the Tor Project, a US nonprofit organization dedicated to advancing human rights and defending online privacy through free software and open networks.
Invention and Purpose
- Tor Browser was invented by a group of computer scientists and privacy advocates to provide a tool for individuals to protect their online privacy and anonymity.
- The initial development of Tor (The Onion Router) began in the mid-1990s at the United States Naval Research Laboratory. It was later released as an open-source project in 2002.
- The primary purpose of Tor Browser is to protect users’ online privacy by routing their internet traffic through a network of volunteer-operated servers called “Tor relays.” This routing process helps to conceal a user’s IP address and encrypt their internet traffic, making it difficult for anyone to track their online activities.
How It Works:
Tor Browser works by utilizing the Tor network to provide privacy and anonymity to its users. It achieves this through a process called onion routing, which involves encrypting and rerouting web traffic through a series of different servers or nodes in the Tor network.
Onion Routing:
Tor Browser employs onion routing to encrypt and reroute web traffic. When you use Tor Browser, your data is encrypted and transmitted through a series of network nodes, known as relays or routers. Each relay in the circuit peels away a layer of encryption, until the data reaches its final destination fully decrypted.
Three Layers of Network Nodes:
The Tor circuit consists of three types of network nodes:
a. Entry/Guard Node:
When you start using Tor Browser, it randomly connects to a publicly known entry node. This entry node introduces your data into the Tor circuit.
b. Middle Nodes:
After your data is encrypted, it passes through a series of middle nodes. Each middle node only knows the identity of the preceding and subsequent middle nodes, ensuring anonymity.
c. Exit Node:
Once the last layer of encryption is peeled off, the decrypted data leaves the Tor network through an exit node and reaches its final server destination.
Anonymity and Privacy:
By routing your web traffic through multiple relays, Tor Browser hides your IP address and browsing activity. This makes it difficult for anyone, including your internet service provider (ISP) and websites you visit, to track your online activities.
Fingerprinting Prevention:
Tor Browser is designed to prevent websites from identifying you based on your browser configuration. It aims to minimize the ability of websites to track and fingerprint users.
Limited Browsing History:
By default, Tor Browser does not retain any browsing history. Cookies are only valid for a single session, until Tor Browser is turned off or a new session is started.
How to Download And Install Tor Browser:
Tor Browser is available for Windows, Mac OS, Android and Linux.
- Proceed to https://www.torproject.org/download/ and choose your operating system.
- Click on the download button and you will be redirected to a download URL. A few seconds later, the download will start.
- The EXE file will be for both 64-bit and 86/32-bit systems.
- After the download is finished, click on the installer.
Installation:
- Choose a language for the setup.
- Set the install location for the browser.
- Start the installation, it will take 1-2 minutes to complete depending on your system specifications.
- You can choose to start the browser at the end and whether to add Start Menu and Desktop Icons.
Accessing the Dark Web:
Open the browser and you will be greeted by this interface:
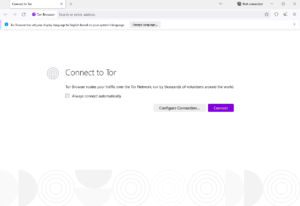
After that:
- You can choose to connect with the default settings and then you will browse the dark web anonymously.
- You can configure the settings for extra protection and safety.
Configuration:
- Click on the Configure Connection button.
- On the left panel, click on Privacy & Security.
- Scroll down to Security.
- There you can choose between Standard, Safer and Safest while sacrificing your functionalities for safety.
- Connect and Surf safely!
That’s it, folks! Now you can explore the dark web anonymously while protected by triple layers, just like an onion.
Be Careful:
Use a VPN for added security:
While Tor provides anonymity, using a VPN (Virtual Private Network) can add an extra layer of security. A VPN encrypts your internet traffic and hides your IP address, making it harder for anyone to track your online activities.
Be cautious of phishing sites and scams:
The dark web is known for its criminal activities, scams, and phishing sites. Exercise extreme caution when clicking on links or accessing websites. Verify the URLs from multiple sources and be wary of suspicious links.
Avoid revealing personal information:
Do not provide any personal information, such as your real name, address, or financial details, while browsing the dark web. Remember that anonymity is crucial in this environment.
Disable JavaScript:
Disabling JavaScript in Tor Browser can help protect against certain vulnerabilities and potential attacks. You can do this by going to the Tor Browser settings and adjusting the security level as mentioned above.
Use encrypted communication:
If you plan to communicate with others on the dark web, consider using encrypted communication methods such as PGP (Pretty Good Privacy). Encryption adds an extra layer of security to your messages.
Use digital currencies:
When making purchases on dark net marketplaces, it is advisable to use digital currencies like Bitcoin. Digital currencies provide an additional layer of anonymity compared to traditional payment methods.
Research vendors and websites:
Before engaging in any transactions or interactions on the dark web, thoroughly research vendors and websites. Look for reviews, feedback, and reputation to ensure you are dealing with trustworthy sources.
Protect your device:
Install and regularly update antivirus software to protect your device from potential malware or viruses that may be present on the dark web.
Continue reading: What Does MLS Stand for in Soccer?

